To set up your gateway, you need an active Jedox Cloud Console account with an active VPN subscription.
First, sign in to the , then scroll down to the Connection section. If you have an active VPN subscription, you will see options for VPN settings. Click Add VPN connection.
The next dialog requires you to fill in a number of fields, which are described below.
| Name | Specify a name for your VPN connection. |
| IKE Protocol | Select the Internet Key Exchange protocol. Options are IKEv1 and IKEv2. |
| VPN Password (Pre-shared key) | The value here must match the value used for your local on-prem VPN device. A key is generated by default when setting up a new connection; use the button on the right to copy it to the clipboard. The value specified here must be the same value that you specify when configuring your VPN device. |
| Public IP address | This field shows the public IP address, visible when accessing the VPN connection. |
| Address space | Subnet address range (private network address space for the Jedox VPN gateway). The address space should be in CIDR format and comes automatically with /32 in the address field. Note that 10.0.0.0/16 address space is reserved and cannot be used. |
| Client IP address | If you have a static public IP address allocated by your internet service provider for your VPN device, enter the IP address here. This will be the public IP address of the VPN device that you want Jedox VPN Gateway to connect to. If you don't have the IP address at this time, you can enter a placeholder IP (i.e., 4.3.2.1), but Jedox Gateway won't be able to connect until the legitimate IP has been entered. |
| Client address space |
Refers to the IP address ranges for the network that this local network represents. You can add multiple address space ranges, but make sure the ranges specified don't overlap with the ranges of other networks that you want to connect to. Add IP / Subnet: you can add additional subnets for your on-premises site(s) in CIDR format (e.g. 192.168.0.0/24). Use multiple connections: by default, multiple subnets are used per CHILD_SA. If the on-prem device does not support multiple subnets per CHILD_SA, then check the box to use multiple connections. |
The VPN connection is then configured for all instances within the organization.
IPsec / IKE policy
For communications that require specific cryptographic algorithms or parameters due to compliance or security requirements, the Jedox VPN gateway can be configured to use a custom IPsecc / IKE policy with specific cryptographic algorithms and key strengths, rather than the default Jedox policy sets.
Advanced settings
Here you can configure MTU / MSS parameters and Dead Peer Detection (DPD) settings. MTU / MSS settings cannot be changed. DPD is turned on by default, and if a dead endpoint is detected, it triggers a re-negotiation.
Routing and Firewall
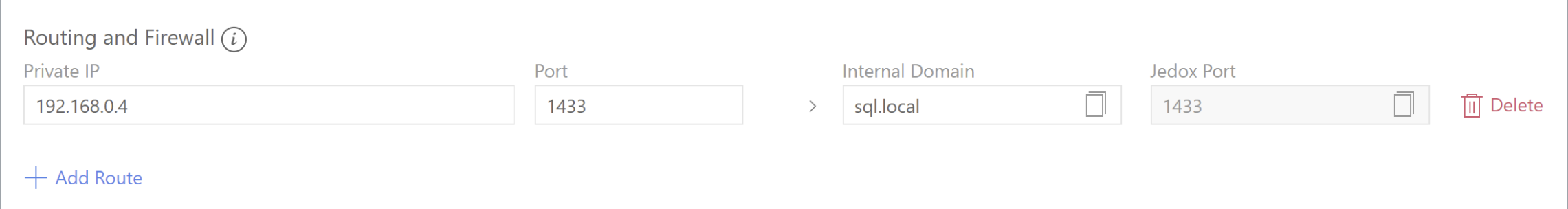
| Client IP |
Private IP of the on-prem internal database. The client IP must be included in the previously entered Client Address spaces. |
| Client Port | Port for the on-prem database. |
| Jedox Domain | Used for the Integrator connection . |
| Jedox Port | Used for the Integrator connection. The Jedox Port is always the same as the Client Port and cannot be changed. |
Below is an example with private IP 192.168.0.4, port 1433, and internal FQDN sql.local.
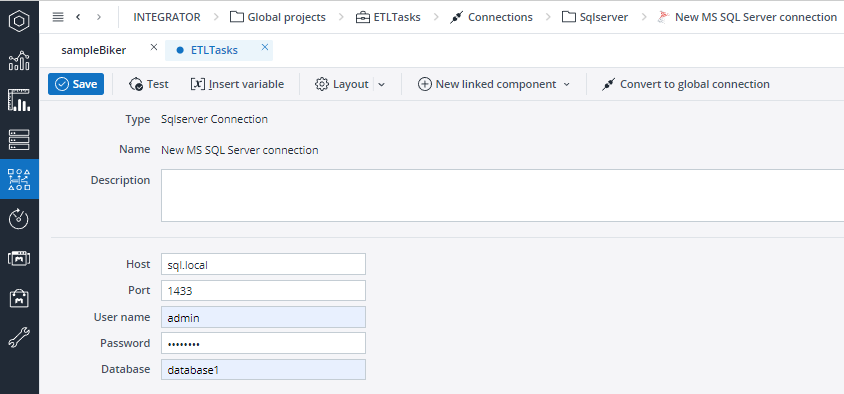
To connect from Jedox Integrator to the above local SQL example, you would set up an Integrator SQLserver Connection with the Jedox domain as Host and the Jedox port as Port:
Managing the VPN
The pre-shared key is a form of password for secure authentication to your Jedox VPN gateway. In the Cloud Console, you can opt to display or hide the key, copy, and edit it.
You can edit existing connections by clicking on the pencil button next to the desired connection.
Note that adding or changing routes (or modifying the VPN tunnel configuration in any other way) will cause Integrator and other services (such as Spreadsheet Server and Web Backend) to restart, which will interrupt any ETL jobs, Jedox Web user sessions, or processes in progress.
Troubleshooting VPN connections
Two different types of errors can occur when setting up a VPN connection:
 An error has occurred
An error has occurred
The VPN tunnel could not be established.
We recommend that you try the following steps:
- Check the negotiation ports
Make sure that ports 500 and 4500 are opened for the VPN negotiation. - Set your VPN device to "Receiver Only"
Configure your VPN device to be the receiver, since Jedox is the initiator of the connection. - Verify Public IP addresses
Check if the correct Public IP address has been entered. - Look in the logs for requests from the Jedox IP address (51.104.148.158)
If there are no log entries from this IP address, try enabling the debug logs and check again. - Check VPN device and Cloud Console settings
Make sure that your VPN device and the settings from the Cloud Console match, e.g. encryption algorithm, hashing algorithm, Diffie-Hellman group, Lifetime in phase 1 and phase 2. - Check the PSK
Verify that the Pre-Shared Key (PSK) is matching your VPN device. - Try another IKE protocol
If the tunnel is still not connecting, try the other IKE protocol (IKEV1 or IKEV2). - Activate the option "Use multiple connections"
If multiple subnets are used, activate the "Use multiple connections" option. - Contact Jedox Support
If the above steps do not work, create a ticket to Jedox Support, mentioning the error you receive and all the tests you have performed.
 One or more routes could not be reached
One or more routes could not be reached
The VPN tunnel has been established, but we could not reach all routes.
Jedox Cloud Console unsuccessfully tried accessing the IP / port specified in the "Routing and Firewall" section. You can see which route is unreachable when you edit the VPN connection. This route will be highlighted in yellow.
We recommend that you try the following steps:
- Check if NAT-T is enabled on your VPN device
NAT-T must be enabled on your VPN device to enforce NAT encapsulation, as we are natting all traffic through the Jedox VPN Gateway. - Look in the logs for requests from the Jedox IP address (51.104.148.158)
If there are no log entries from this IP address, try enabling the debug logs and check again. - Investigate your network
Further investigate your network, e.g. the firewall or other rules. - Contact Jedox Support
If the above steps do not work, create a ticket to Jedox Support, mentioning the error you receive and all the tests you have performed.
Updated September 26, 2025