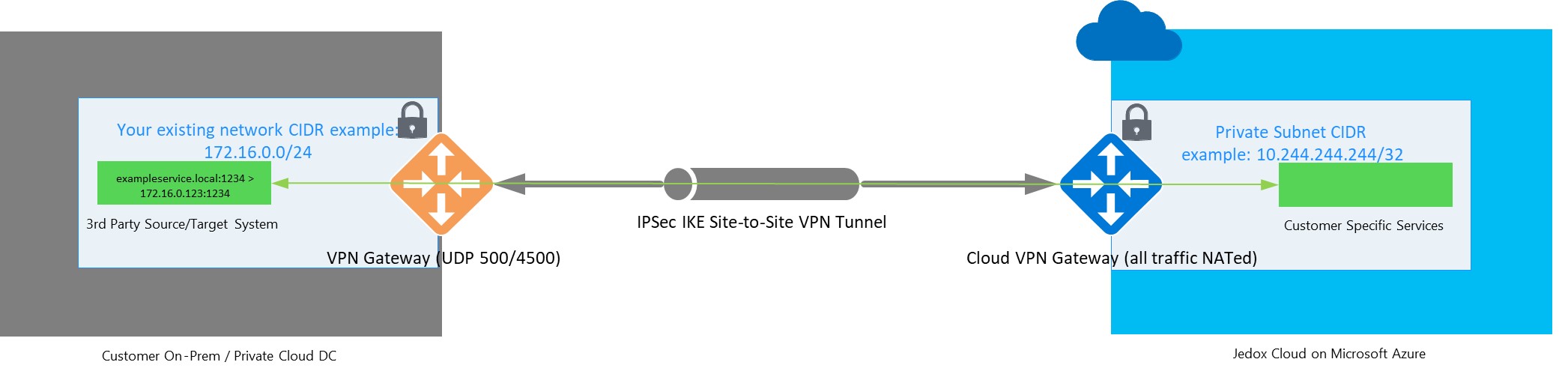
Cloud Virtual Private Network (VPN) Gateway establishes a secure site-to-site VPN tunnel between Jedox Cloud and the customer’s corporate network using industry-standard encryption algorithms called IPSec. Site-to-site IPsec VPN is a secure network protocol suite that authenticates and encrypts the packets of data to provide secure encrypted communication between two private networks (Jedox Cloud and the customer's network) over the public internet.
Benefits:
- Fully supported implementation through guided onboarding process
- Industry-standard security protocols: IPSec and IKEv1 and IKEv2 supported
- Self-service connection status monitoring and control in Jedox Console
- Both policy-based and route-based IPSec configuration
- Use your existing internet connection
- Site-to-site VPN
Use cases:
- Connect Jedox Cloud to your headquarters, branch locations, or private data centers where third party data resides, so that you can connect to them, ingest and aggregate data in Jedox.
- Securely connect to workloads in other providers’ cloud services.
- Connect multiple locations to the Jedox Cloud.
Prerequisites
To setup the VPN connection, you need the following information:
- Customer’s VPN Gateway’s public IP address; to negotiate IPSec connection, UDP ports 500 and 4500 have to be open.
-
Gateway subnet address range (private network address space of the customer); e.g. CIDR example: 172.16.0.0/24; Please note it cannot be 10.0.0.0/16 as it is reserved.
- Specific routes: the whole network on customer end is usually visible after connection is established. If not, specific routes, private IP's, ports, and FQDNs used by the business users have to be explicitly defined, e.g. sqlserver.mynet.local > 172.16.0.123:1433
- Name and firmware version of the VPN device.
Additionally, you must clamp TCP MSS at 1350. If your VPN devices do not support MSS clamping, you can alternatively set the MTU on the tunnel interface to 1400 bytes instead.
Border Gateway Protocol (BGP) and High Availability (HA) are currently not supported.
VPN Compatibility Note
While Fortinet FortiGate appliances are widely used, they may not always be fully compatible with the Jedox VPN configuration. In certain cases, specific FortiGate settings or firmware versions can cause connectivity issues or prevent the VPN tunnel from establishing correctly.
Although basic site-to-site IPsec setups may work under strict conditions, advanced features such as BGP routing and High Availability (HA) are not supported, as they can lead to unreliable integrations. Supported scenario: only standalone IPsec VPN configurations may function if FortiGate is configured with Jedox’s specific IKE parameters.
For best reliability, performance, and support, we strongly recommend using Azure, Palo Alto, Sophos, and Cisco devices. Depending on the firmware version, these devices are supported and provide a seamless, stable connectivity with the Jedox environment.
See also Setting Up a VPN Gateway.
Default IPsec / IKE parameters
| Phase 1 | Authentication method | Pre-shared key |
| PSK | Unique 16-character string, include symbols, numbers, lowercase, uppercase characters | |
| Encryption scheme | IPSec(IKEv2 for both phases) | |
| Diffie-Hellman group | 2 (1024-bit key lengtht) | |
| Encryption algorithm | AES256 | |
| Hashing algorithm | SHA256 | |
| Main or aggressive mode | Main mode | |
| Lifetime (for renegotiation) | 28800 seconds | |
| Phase 2 | Encryption algorithm | AES256 |
| Authentication algorithm | SHA256 | |
| Perfect Forward Secrecy | None | |
| Lifetime (for renegotiation) | 27000 seconds |
Updated January 19, 2026