Each connection that you set up inside an Integrator project has a number of controls that determine who has access to the data and under what conditions.
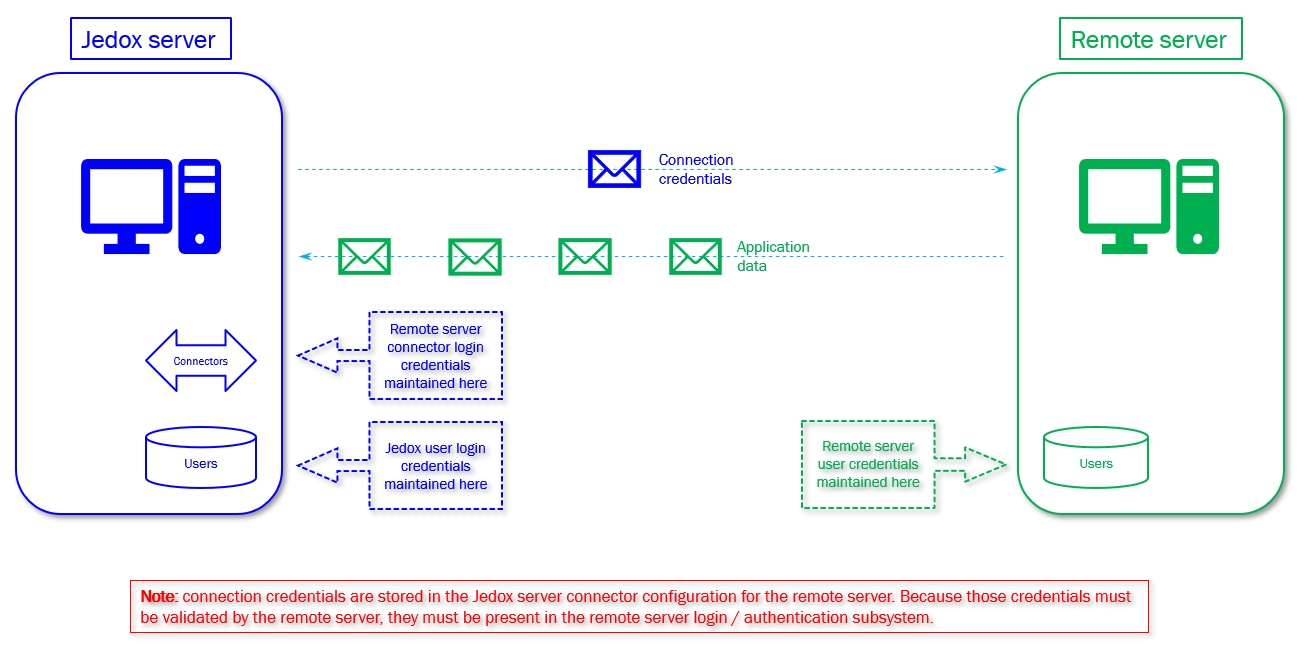
First, the logged-in Jedox user credentials (such as local security credentials or an SSO mechanism) are not the same credentials that are used for Integrator connections. Each Integrator connection has its own specified credentials that are used to establish the connection to the remote system.
Connection credentials are stored in the Jedox server in one of two locations:
- Integrator projects: an Integrator project may contain several connections of different types.
- Global Connection Manager: connections are stored individually and may be referenced from Integrator projects.
So, in the case of Power BI, for example, the user may log in to Jedox as ann.user@customer.com, but the connection to Power BI will specify a particular set of credentials that are valid to the Power BI system but have no validity at all in the Jedox system. Those credentials could also be AD-derived, but they could be purely local to the Power BI system.
Regardless of WHO is logged into the Jedox system, if they are allowed to use this particular connection, they will have access to any data and applications on the Power BI end that are allowed by the connection-specified credentials.
For example, if you have a large number of users who are not Jedox experts, you may have a small team (or a consultant) who defines a single connection, using purposefully defined Power BI login credentials, to allow that large group of users to access Power BI data from Jedox Suite. Equally, you could specify multiple connections, each using different credentials, and each restricted to a smaller Subset of your users. (That Subset could be as small as one single user.)
However, there are two additional levels of control available to the customer, based on two storage locations mentioned above:
- Integrator projects: each Integrator project has, in its properties settings, a security control that allows you to restrict use (including visibility) of the connection to specified Jedox users. If a user is not specified in this listing, they cannot use the connection, cannot access any of the data at the remote Power BI end, and cannot even see the connection. If the user is specified in these security properties of the connection, they can still be prevented from seeing or changing the credentials used by the connection.
- Global Connection Manager: there’s a similar set of global connection controls that restrict Jedox user access to globally defined connections.
Whether or not a Jedox user has, via the Power BI (or Qlik, or SAP, etc.) connection, access to data or applications owned by other users depends totally on the rights assigned to the credentials used in the connection, and not to any property of the local Jedox user.
IF (1) the Jedox user has the right to use a connection, and
IF (2) that connection contains credentials that have rights to that connection's data or applications,
THEN (3) by using this connection, the Jedox user has the ability to access the same data or applications;
ELSE (4) they do not.
Updated July 3, 2025